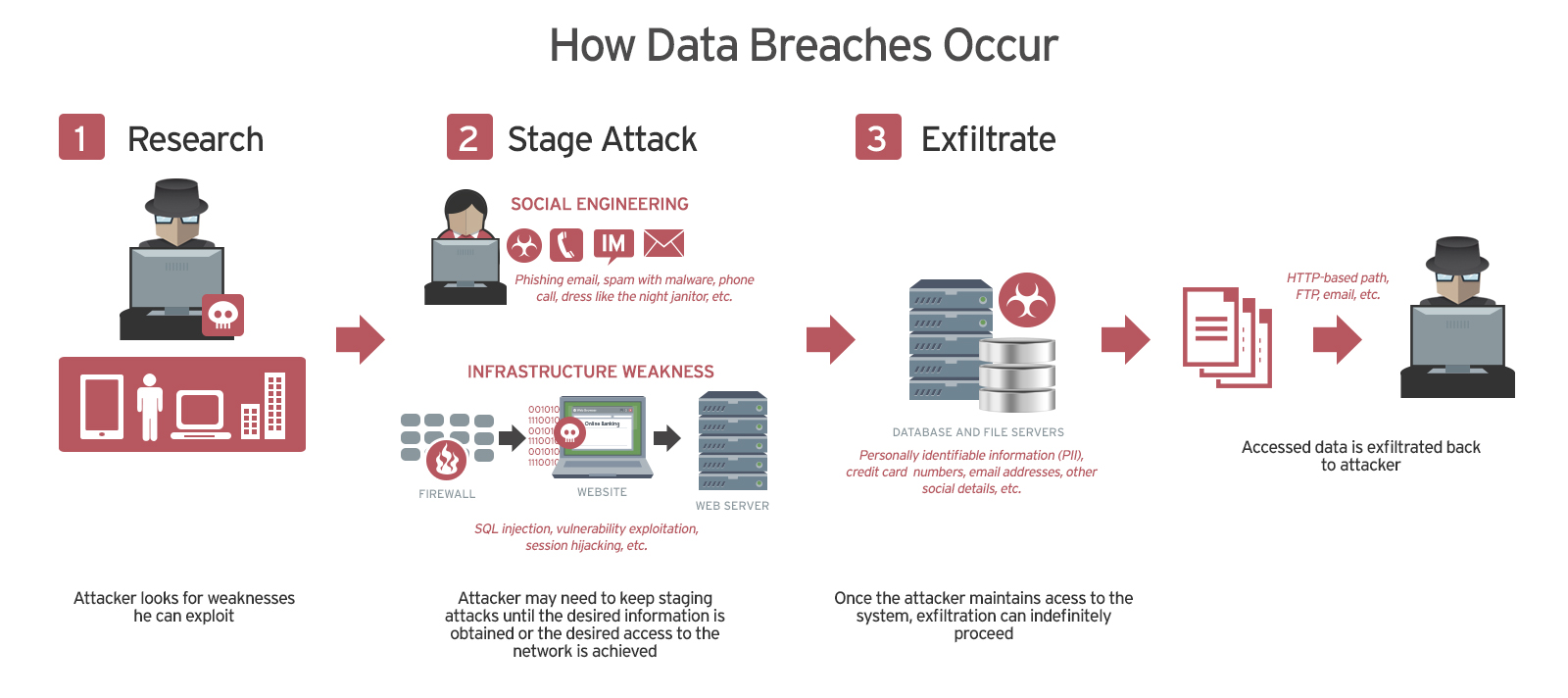
A recent study shows a growing demand for Data Openness and Data Sharing from the wider research community in today’s world. Many funding bodies are insisting to change researcher attitudes and practices around data by bringing openness and reproducibility of research. These bodies are also providing the guidance and tools to the communities to increase the transparency of research data. Data sharing is an integral aspect of this development.
There is also a growing demand for sharing Medical Information and Clinical Data as a public good. An Openness of Medical Information raises a big question concerning the safety and security of individual patient records. Maintaining confidentiality of data records is also very important. A public trust perception in the entire healthcare establishment is directly linked to the privacy of their medical records which it keeps. Privacy of the medical records is also a significant factor in discussions of health data sharing. The complex issue has many challenging dimensions, from what happens after the initial intake of an individual’s data to what happens in data aggregation and secondary use. There are many key legal and social challenges to privacy issues from a variety of perspectives.
Importance of Data Sharing in Healthcare
Most of public surveys results indicate that the public holds strong privacy concerns about how their personal health information is handled. Surveys also show that peoples are mostly concerned about the uses of their private data not directly relevant to providing care. These surveys also indicate that current laws and organizational practices may not provide adequate privacy protection for patients.
On the other hand, many research organizations recommend a scope of activities related to health privacy, patient notice, and public education on privacy and compliance as opportunities to provide evidence-based medicine (EBM). With the increased incorporation of electronic health records (EHRs) into care delivery and research, the growing volumes of valuable data for evidence-based research and care may eventually force significant changes to strike a balance between privacy and advancement.
Balancing patient privacy protections with advancing data-driven clinical research and care delivery is an ongoing challenge for many healthcare organizations. Some researchers suggest that patient-controlled privacy policies, such as those offered through repositories of personal health records, might help with gaining traction on the issues of clinical data, privacy, and security with the public. They also recommend a scope of activities related to health privacy, patient notice, and public education on privacy and compliance as opportunities to provide evidence-based medicine (EBM).
The Ups and Downs of Evidence Based Medicine
https://youtu.be/9wh_1n85HBc